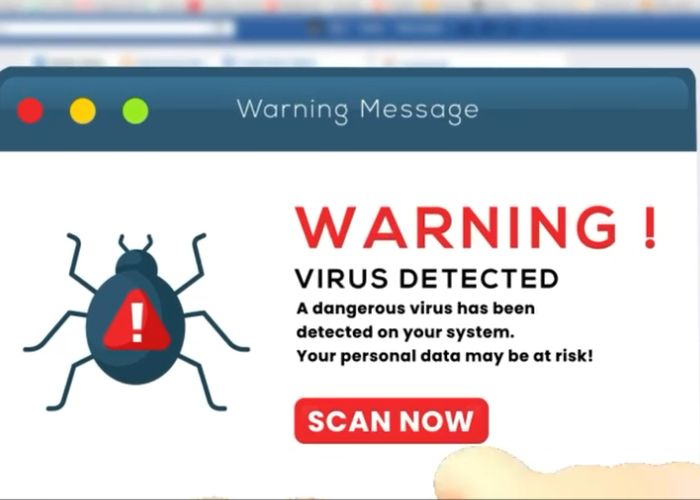
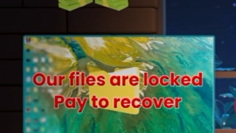
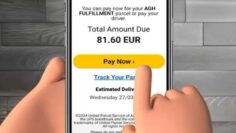
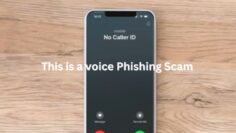
Home Online Threats Awareness Recognizing Suspicious Pop-Up Scams: How to Protect Your Computer from Malicious Pop-Ups
-
-
No videos yet!
Click on "Watch later" to put videos here
- View all videos
-
-
- 0
-


.png)