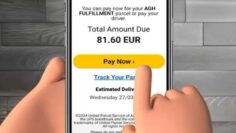
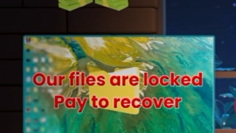
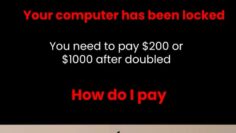
Home Online Threats Awareness Protecting Secure Areas: Preventing Tailgating and Unauthorized Access
-
-
No videos yet!
Click on "Watch later" to put videos here
- View all videos
-
-
- 0
-


.png)