Phishing Attacks Are Evolving: Never Share Your 2FA Code!
Phishing Attacks Are Getting Smarter: Never Share Your 2FA Code
Cybercriminals are constantly evolving their tactics to steal sensitive information. While strong passwords are essential, they are no longer enough to keep your accounts secure. That’s why many people rely on two-factor authentication (2FA) as an added layer of protection. However, attackers have adapted and now use sophisticated phishing scams to trick users into handing over their 2FA codes.
In this article, we’ll explore how these phishing scams work, common tricks used by scammers, and most importantly, how you can protect yourself from falling victim.
How Phishing Attacks Target 2FA Security
Two-factor authentication (2FA) is one of the most effective ways to secure your online accounts. It requires a second form of verification, such as a temporary code sent via SMS, email, or an authenticator app. Even if a hacker steals your password, they still need this code to gain access.
However, cybercriminals have developed phishing techniques to bypass 2FA security. Let’s look at a real-world example:
A Common Phishing Scenario
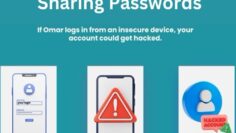
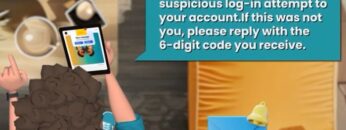
Omar receives a text message that appears to be from his email provider. The message warns him of suspicious activity on his account and urges him to verify his identity by clicking a link. The link directs him to a page that looks exactly like his email provider’s login page.
He enters his email and password. Immediately, the fake site asks for his 2FA code, claiming it’s required to secure his account. Thinking it’s a legitimate request, Omar enters the code.
Within seconds, hackers use the stolen credentials and 2FA code to log into his actual account. They can now change his password, lock him out, and steal his personal data.
How Cybercriminals Steal 2FA Codes
Attackers use several techniques to trick users into revealing their authentication codes. Some of the most common include:
1. Fake Urgent Messages
Scammers create a sense of urgency, sending emails or SMS messages that claim:
- Your account has been locked due to suspicious activity.
- There was an unauthorized login attempt.
- You need to verify your identity to prevent deactivation.
Victims are pressured into acting quickly, clicking malicious links, and providing their login credentials and 2FA codes without verifying the source.
2. Spoofed Websites
Cybercriminals create fake websites that mimic real ones, complete with identical logos, fonts, and layouts. The goal is to trick users into believing they are logging into a legitimate service while actually handing their information over to attackers.
3. Social Engineering Calls and Messages
Sometimes, scammers will call victims pretending to be from IT support, customer service, or even a financial institution. They claim they need the victim’s 2FA code to fix an issue or verify their identity. In reality, they are attempting to gain unauthorized access.
4. Real-Time Session Hijacking
Some advanced phishing attacks operate in real time. Attackers use stolen credentials and 2FA codes immediately, logging in before the code expires. This method is especially dangerous because victims might not realize they’ve been hacked until it’s too late.
How to Recognize Phishing Attempts
To protect yourself, always be on the lookout for these phishing red flags:





How to Protect Yourself from 2FA Phishing Scams
1. Never Share Your 2FA Code
Your 2FA code is private and should never be shared with anyone—not even customer support. Legitimate companies will never ask for it.
2. Use an Authenticator App Instead of SMS 2FA
SMS-based 2FA is more vulnerable to phishing and SIM-swapping attacks. Consider using an authenticator app like Google Authenticator or Microsoft Authenticator for added security.
3. Verify Links Before Clicking
Before clicking any link in an email or text, check the sender and hover over the link to see where it really leads. If in doubt, go directly to the company’s official website instead.
4. Enable Phishing Protection Tools
Many web browsers and security software offer phishing protection features that warn you about suspicious sites. Keep these tools enabled at all times.
5. Report Phishing Attempts
If you receive a suspicious email, text, or call, report it to the company it claims to be from. You can also report phishing emails to organizations like Google and Microsoft to help prevent future attacks.
6. Use Strong, Unique Passwords
Even with 2FA enabled, a strong password is essential. Avoid using the same password across multiple sites, and consider using a password manager to keep track of them securely.
Conclusion
Phishing scams continue to evolve, and cybercriminals are finding new ways to trick users into giving up their 2FA codes. While two-factor authentication is a powerful security measure, it’s only effective if you remain cautious and vigilant.
By recognizing phishing tactics, staying aware of red flags, and following best security practices, you can keep your accounts safe from cyber threats.

Stay safe, stay smart, and protect your online identity.


.png)