The Fake Tech Support
How to Recognize and Avoid Impersonation Scams
Introduction
In today’s digital landscape, cybercriminals continuously develop new strategies to trick individuals and organizations. One prevalent method is the Fake Tech Support scam, where scammers impersonate trusted service providers to gain remote access to devices or obtain sensitive information. In this guide, we will explore the tactics used by these fraudsters, highlight the warning signs, and offer actionable steps to protect yourself and your organization from falling victim to these schemes. Recognizing and understanding these scams is critical in maintaining digital security and ensuring that you never inadvertently compromise your personal or professional data.
Understanding the Scam Tactics
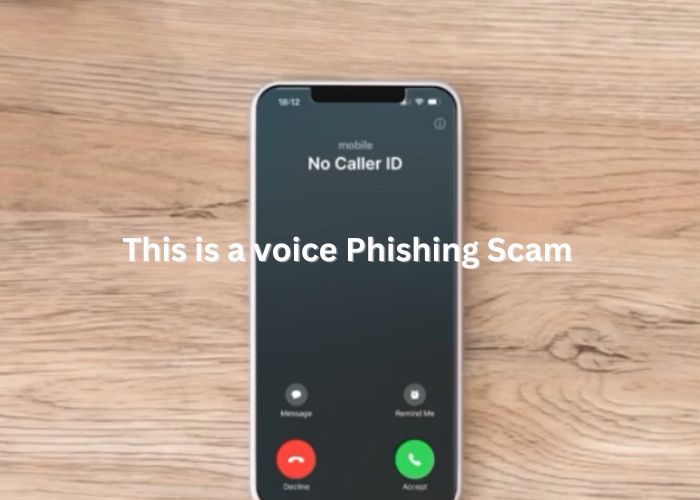
Scammers who engage in such fraudulent activities often use sophisticated social engineering techniques to create a sense of urgency and panic. In one scenario, an individual named Omar receives a call from someone claiming to be from his internet provider. The caller, using a friendly yet authoritative tone, warns about unusual activity on his connection and insists that remote access is necessary to fix the supposed issue. This behavior is characteristic of a Fake Tech Support operation, aiming to bypass rational decision-making and prompt immediate action without proper verification. By understanding these tactics, you can better equip yourself to recognize fraudulent behavior and protect your digital assets.
Warning Signs to Watch For
Certain red flags can help identify a scam of this nature. First, the unsolicited nature of the call should raise concerns; genuine service providers rarely initiate contact without prior communication. Additionally, the use of high-pressure language that demands immediate action is a common characteristic of these scams. If a caller insists that urgent steps are required to resolve an issue, it is wise to remain cautious. Moreover, requests for remote access or sensitive login credentials are a significant indicator of fraudulent activity. Even if the call appears legitimate, always be skeptical of any request that deviates from standard security protocols. Awareness of these warning signs is your first line of defense against impersonation attacks.
Best Practices for Verification
When faced with a suspicious call or message, it is crucial to take a step back and verify the request through official channels. If you receive a call from someone claiming to be tech support, hang up immediately and contact your service provider using the phone number listed on their official website or your account documentation. Never rely on the contact information provided in the suspicious message. Always be wary of Fake Tech Support requests that demand immediate access or sensitive details. Additionally, consult with colleagues or your IT department if you are in a corporate environment. Verifying the legitimacy of the call through multiple sources not only helps protect your data but also prevents the potential spread of the scam within your organization.
The Importance of Employee Awareness
Organizations must prioritize regular training and awareness programs to educate employees about common scams, including those involving tech support impersonation. Employees who are well-informed about the tactics used by cybercriminals are less likely to fall prey to these scams. In the scenario discussed, the timely intervention of colleagues who recognized the warning signs prevented a potential security breach. Regular simulated phishing exercises and training sessions can reinforce best practices, ensuring that employees know how to verify suspicious requests effectively. Cultivating a culture of vigilance and accountability within the workplace is vital in mitigating the risks associated with impersonation and social engineering attacks.
Practical Steps to Enhance Security
In addition to personal vigilance, implementing robust security measures can further protect against these scams. One effective strategy is to establish clear protocols for verifying any technical support requests. For instance, organizations can create dedicated hotlines or verification procedures that employees must follow when receiving unexpected communications regarding IT issues. Employing multi-factor authentication adds an extra layer of security, making it significantly more challenging for scammers to gain unauthorized access even if they manage to obtain some credentials. Regularly updating software, conducting security audits, and keeping abreast of the latest scam trends are all critical steps in strengthening your overall security posture.
Conclusion
Fake Tech Support scams represent a serious threat in our increasingly digital world. By exploiting trust and using urgent language, scammers are able to manipulate even the most cautious individuals. By following these guidelines, you can effectively avoid falling victim to Fake Tech Support scams. Recognizing the warning signs, verifying requests through official channels, and maintaining a high level of awareness are essential strategies in combating these fraudulent tactics. This guide has provided an in-depth look at how these scams operate, the risks involved, and the best practices for staying secure. Taking proactive steps to educate yourself and your colleagues can help ensure that you are never caught off guard by these deceptive schemes.
Final Thoughts
In summary, being aware of the dangers posed by impersonation scams is the key to preventing them. Whether you are an individual or part of an organization, always prioritize verification and caution when approached with unexpected technical support requests. The measures outlined in this guide—ranging from understanding scam tactics to implementing robust security protocols—serve as a comprehensive roadmap to protect your digital life. Remember, if something feels off or too urgent, it is always better to verify through trusted and official sources. Stay informed, stay secure, and never let scammers compromise your digital safety.
personal information.


.png)