Preventing Locked Screen Ransomware Attacks: A Comprehensive Data Protection Guide
Preventing Locked Screen Ransomware Attacks: A Comprehensive Data Protection Guide
Introduction to Ransomware Threats
In today’s increasingly digital environment, cyber threats continue to evolve, with one of the most alarming being locked screen ransomware attacks. In this scenario, an individual named Omar opens an email attachment that triggers a sudden, terrifying lockdown of his computer screen with a ransom message demanding payment to unlock his files. This incident serves as a powerful reminder of the critical importance of being cautious with email attachments and remaining vigilant against scams. Ransomware, which exploits vulnerabilities in our systems, can quickly paralyze work and compromise sensitive data if proper preventive measures are not in place.
Understanding the Locked Screen Ransomware Attack
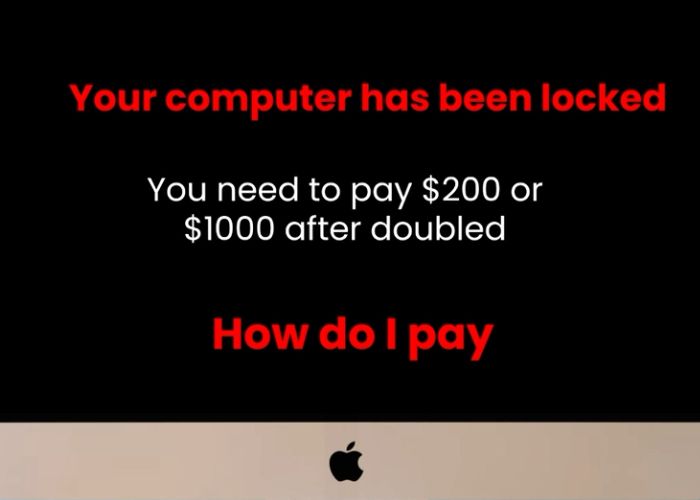
Locked screen ransomware attacks typically begin with a seemingly ordinary email that contains an attachment. When opened, the attachment executes malicious code, encrypting files or locking the entire system and displaying a ransom note. In our scenario, Omar experiences a rapid shift from routine work to panic as his computer becomes inaccessible. The attacker’s demand for money to restore access is designed to force a quick decision before the victim has time to consider the consequences. This type of attack is a stark example of how ransomware can be used as a tool for extortion, with criminals banking on the victim’s desperation to regain control over their data.
Ransomware Warning Signs to Recognize
Several warning signs can help you identify a potential ransomware attack before it fully unfolds. First, be wary of unsolicited emails, especially those with attachments from unknown or unexpected sources. In Omar’s case, the email attachment was the trigger for the ransomware attack. Second, any sudden change in system behavior—such as an unexpected lock screen or a message demanding payment—should immediately raise red flags. It is crucial to note that legitimate companies and service providers will never lock your device and demand payment in this manner. Recognizing these indicators early can prevent further damage and help you take immediate action.
Immediate Steps to Take Against Ransomware
If you find yourself in a situation similar to Omar’s, it is important to act quickly and calmly. The first step is to disconnect your computer from the internet to prevent the ransomware from communicating with its command-and-control server or spreading to other devices on your network. This isolation is vital for limiting the damage. Next, do not attempt to pay the ransom or follow any instructions provided in the ransom note. Instead, seek professional assistance from your IT department or a trusted cybersecurity expert. Reporting the incident immediately can also help protect others within your organization from similar attacks.
Best Practices for Ransomware Prevention
Preventing locked screen ransomware attacks involves a combination of good cyber hygiene and robust security practices. One of the most effective measures is to avoid opening email attachments from unverified sources. Always verify the sender’s identity before downloading or executing any files. Additionally, ensure that your computer is equipped with up-to-date antivirus software that can detect and block malicious activity before it causes harm. Regular software updates and system patches are also essential, as they close security gaps that ransomware can exploit. Backing up your data frequently is another key element of prevention. With reliable backups, you can restore your files without having to comply with ransom demands, thereby minimizing the overall impact of an attack.
The Role of Backups and Antivirus Software in Combating Ransomware
In our scenario, one of the critical pieces of advice came from a colleague who reminded Omar that having backups can be a lifesaver. Backups provide a secure way to recover your data in the event of a ransomware attack. Coupled with updated antivirus software, which serves as the first line of defense against malware, these measures form a robust barrier against ransomware. Antivirus programs work by scanning attachments and detecting suspicious behavior, alerting you before the threat materializes. When combined with regular data backups, they ensure that even if an attack occurs, you can quickly restore your system to a pre-attack state without succumbing to the attackers’ demands.
Employee Awareness and Training on Ransomware Threats
An essential aspect of defending against ransomware is ensuring that all employees are well-informed about the risks and best practices. Regular training sessions can help staff recognize the signs of phishing emails and other social engineering tactics. In many cases, like Omar’s, a quick word of caution from a knowledgeable colleague can prevent a costly mistake. Organizations should invest in comprehensive cybersecurity awareness programs that include simulated phishing exercises and detailed guidelines on handling suspicious emails. By fostering a culture of vigilance, companies can reduce the likelihood of ransomware incidents and protect sensitive information across all levels.
Practical Security Measures for Organizations to Prevent Ransomware
Beyond individual vigilance, organizations should implement practical security measures to mitigate the risks posed by ransomware. Establishing clear protocols for handling email attachments, including verification steps before opening any file, is essential. Companies can also deploy network segmentation strategies to limit the spread of malware if an infection occurs. Multi-factor authentication (MFA) adds an extra layer of security, making it significantly more challenging for attackers to gain unauthorized access to sensitive systems. Regular security audits and vulnerability assessments are also recommended, as these practices help identify and address potential weaknesses in your IT infrastructure before they can be exploited by cybercriminals.
Conclusion: Staying Safe from Ransomware
Locked screen ransomware attacks are a serious and growing threat that can paralyze your digital environment and compromise vital data. By understanding the tactics used by cybercriminals, recognizing the warning signs, and implementing robust preventive measures, you can protect yourself and your organization from these malicious attacks. Always be cautious when opening email attachments, keep your antivirus software updated, and maintain regular backups to ensure that your data remains secure. The case of Omar highlights the critical importance of taking immediate, informed action when faced with unexpected digital threats.
Final Thoughts on Ransomware Prevention
Ultimately, the key to preventing ransomware lies in education, preparedness, and proactive security measures. Whether you are an individual user or part of a larger organization, it is crucial to remain aware of the risks and be ready to act swiftly if an attack occurs. By following the guidelines outlined in this comprehensive guide, you can significantly reduce the likelihood of falling victim to locked screen ransomware attacks. Stay informed, stay protected, and always verify the authenticity of any communication that seems suspicious. Remember, a cautious approach today can save you from the costly repercussions of a ransomware breach tomorrow.