Beware of Fake Colleagues: Protect Your Workplace from Impersonation Attacks
Hackers are constantly finding new ways to infiltrate systems, and fake software updates have become one of their most deceptive tactics. A pop-up appears on your screen, urging you to install an update for your browser, media player, or security software. But instead of improving
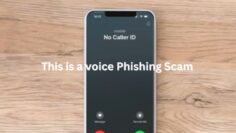
Cybercriminals are increasingly using social engineering tactics to manipulate employees into granting access to sensitive information. In this scenario, Omar receives a chat message from someone pretending to be his colleague, Ahmad, urgently requesting access to a shared drive. Without verification, granting such access could lead to a major security breach.
Key Lessons from This Situation:
🔹 Never assume a message is legitimate just because it comes from a familiar name. Attackers can spoof email addresses, chat accounts, or use stolen credentials.
🔹 Urgency is a red flag. Social engineers create a sense of pressure to make you act without thinking.
🔹 Always verify through a secondary method. Before granting access, call or speak to the person directly using their known contact information.
A simple double-check can prevent a major security incident. Stay alert and always verify before sharing access or confidential information!


.png)